Featured
Table of Contents
- – What Is Openvpn Protocol? - Nordlayer Learn
- – How Vpns Work, And Why You Need One On Your Phone
- – What Is Openvpn? - Review
- – How Does Openvpn Work [The Only Guide You'll ...
- – Openvpn Working With Tcp Not With Udp
- – What Is Openvpn And Should You Use It?
- – Openvpn Over Tcp Vs. Udp: What Is The Differ...
- – 1. Ultimate Powerful Vpn Connectivity
- – How Vpns Work, And Why You Need One On Your ...
What Is Openvpn Protocol? - Nordlayer Learn
It is possible to utilize Open, VPN easily since it is open source, which implies you are complimentary to use it if you follow the conditions in the software license contract. But while the code is free, it's worth explaining that it requires a lot of manual setup (i.
What is it excellent for if it's not super-safe? You might have seen that your VPN breaks this out as two protocols: Open, VPN UDP and Open, VPN TCP.
How Vpns Work, And Why You Need One On Your Phone
What kind of features could guarantee this type of security? A crucial function of Open, VPN is that it is very versatile and one variation can vary from another. So it appropriates for a number of purposes. Your VPN supplier might utilize a different version than what's being utilized by another company.
When they discover a bug, they repair it and they also keep attempting to include brand-new features to it. This is the main reason behind the adaptability of Open, VPN.There are a variety of ciphers supported by Open, VPN. But as a standard, Open, VPN implements 256-bit file encryption, although it's not mandatory (you may have seen some VPN suppliers providing Open, VPN with AES-128 bit file encryption).
What Is Openvpn? - Review
No matter how your VPN provider might pick to set up their servers and connection, Open, VPN will be ideal for them. Open, VPN, on the other hand, can run on Windows, Mac, Android, i, OS, Linux, and other platforms.
Given that Avast is a substantial name in the cybersecurity market, you would anticipate they do not keep any logs. Regrettably, they do. This suggests while the government might not understand what you're doing, the VPN business understands when you visited and when you logged out. And this information can, if required, be turned over to the government.
How Does Openvpn Work [The Only Guide You'll Ever ...
I evaluated 30+ VPNs and found the very best ones that use Open, VPN. It features the protocol pre-configured in addition to its other security protocol choices. It likewise provides unbelievable speeds, is extremely reliable, and keeps your info protected and personal. It's backed by a 30-day money-back guarantee, so you can try Express, VPN risk-free.

This has actually developed a community of VPN protocol programmers and users who constantly test, upgrade, and enhance the procedure. Like any VPN, Open, VPN. Various protocols do this in other, special, and incredibly complex good manners. Making it so nobody can get to your delicate and personal information. by covering it in layers of extra information.
Openvpn Working With Tcp Not With Udp
The "Community Edition" is totally free and has all the basic tools to utilize the web securely. The "Gain access to Server" version comes for a rate with advanced functions so you can tweak the protocol to its greatest abilities. Premium VPNs, like Express, VPN, currently have the procedure preconfigured. Unless you are experienced in manual setup, dealing with Open, VPN can be extremely lengthy and complex.
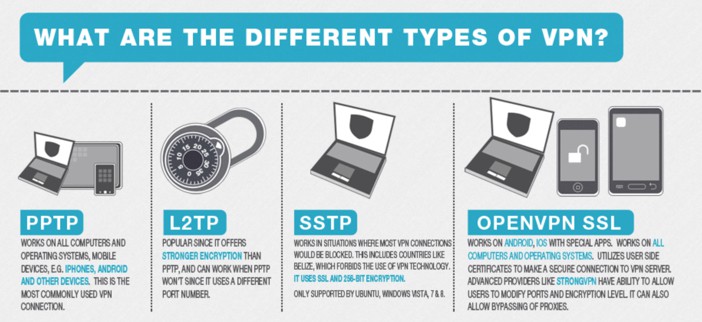
The very same goes for when you utilize Open, VPN via a VPN supplier. Open, VPN works differently based on the settings and setups.
What Is Openvpn And Should You Use It?
SSL/TLS procedures share the keys to encode and translate info sent between devices. These ciphers utilize secrets the elements that "unlock" encrypted messages, for example, 256 0s and 1sts, making them extremely hard to decipher.
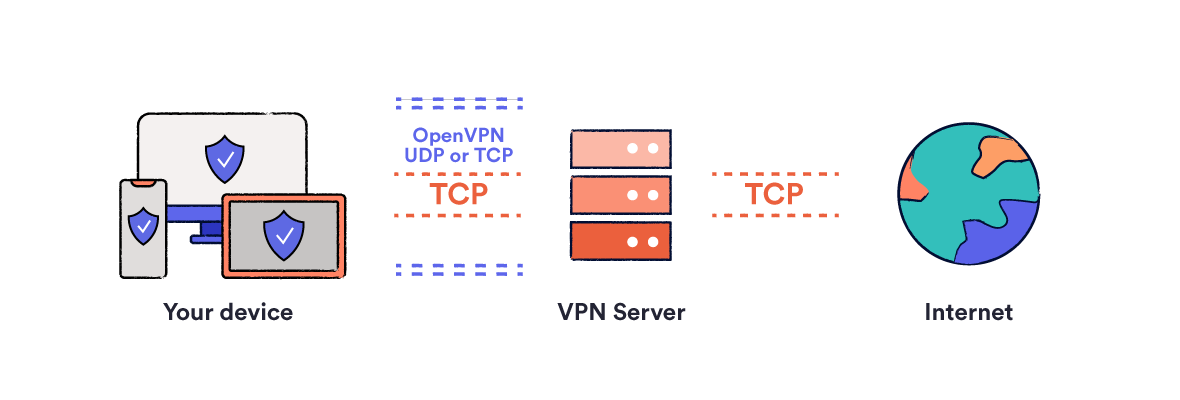
This protocol manages how your information is sent and makes sure whatever sends in the correct order, so there's no jumbling of information. It does this by way of a corrective mechanism within the protocol. TCP makes for a really trusted way to send details. Because it processes your data extremely intently, it can result in slower web speeds.
Openvpn Over Tcp Vs. Udp: What Is The Difference?

VPNs like Cyber, Ghost deal Open, VPN on both Android and i, OS. Due To The Fact That Open, VPN is so popular, some servers and systems look for this protocol and obstruct it. Utilizing Open, VPN with a VPN can assist you avoid this. For example, Express, VPN offers Open, VPN among its procedure selections and can navigate these blocks most of the time.
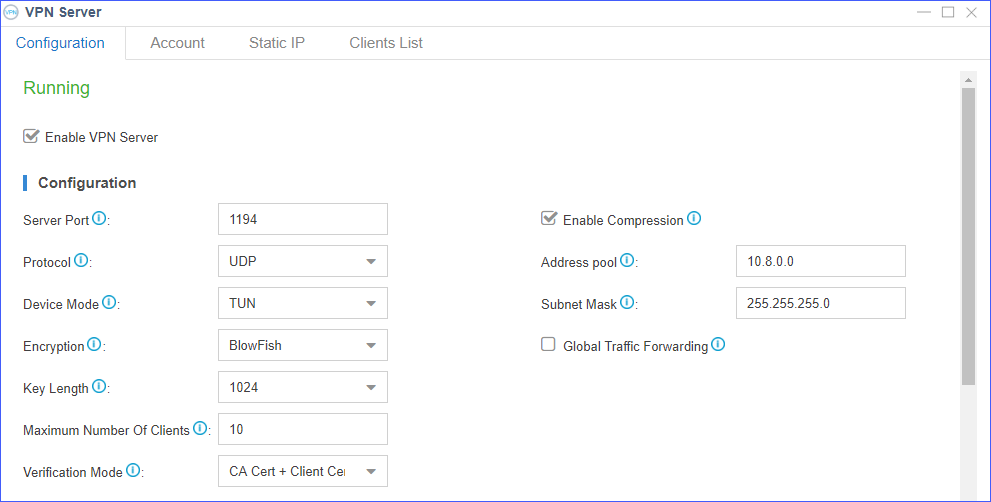
Open, VPN is even typically thought about safe from spying by the NSA (United States National Security Firm), which has sophisticated methods and a big budget, which is extremely remarkable. as an open-source protocol, making it more trustworthy. When a huge company handles a procedure, you have to trust it not to share your information with federal government agencies or other organizations.
1. Ultimate Powerful Vpn Connectivity
Open, VPN offers a list of recommendations to enhance security after installation for that extremely purpose. by ensuring Open, VPN is set up properly. I recommend utilizing a premier VPN, such as Express, VPN, so you can trust that your information remains private. I suggest Express, VPN as Open, VPN comes pre-configured, and it won't compromise your speed.
Go to settings and choose Open, VPN. Pick TCP (more safe) or UDP (much better speeds). You can now search the web, play video games, stream videos, and more with self-confidence that your information is kept personal. Tech-savvy users can do so fairly easily, however there is still space for error in this procedure, and any mistakes could be challenging to repair.
How Vpns Work, And Why You Need One On Your Phone
On top of that, your actual location is secured with IP/DNS leak defense. I utilized ipleak. net to evaluate Express, VPN for leakages and identified none. It does this by changing the file encryption keys often. It would be unreadable even if someone were to get their hands on your data.
Table of Contents
- – What Is Openvpn Protocol? - Nordlayer Learn
- – How Vpns Work, And Why You Need One On Your Phone
- – What Is Openvpn? - Review
- – How Does Openvpn Work [The Only Guide You'll ...
- – Openvpn Working With Tcp Not With Udp
- – What Is Openvpn And Should You Use It?
- – Openvpn Over Tcp Vs. Udp: What Is The Differ...
- – 1. Ultimate Powerful Vpn Connectivity
- – How Vpns Work, And Why You Need One On Your ...
Latest Posts
Best Vpn For Business
What Is A Vpn?
Best Vpns For Small Businesses (2023)
More
Latest Posts
Best Vpn For Business
What Is A Vpn?
Best Vpns For Small Businesses (2023)